0x00 前言
泛微又双叒出问题了,2019年10月24日泛微OA被爆出数据库配置信息泄露,攻击者可通过访问指定页面获取加密的数据库配置信息,下面进行漏洞复现。
0x01 漏洞复现
发生信息泄露的页面为/mobile/DBconfigReader.jsp
访问可查看到一串乱码,返回一行乱码即表明漏洞存在。
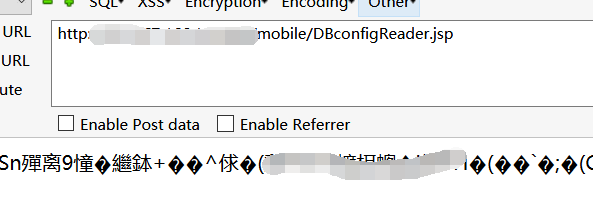
此串乱码即为数据库配置信息经过DES加密后的结果,而默认密钥在源码中可查看为1z2x3c4v5b6n
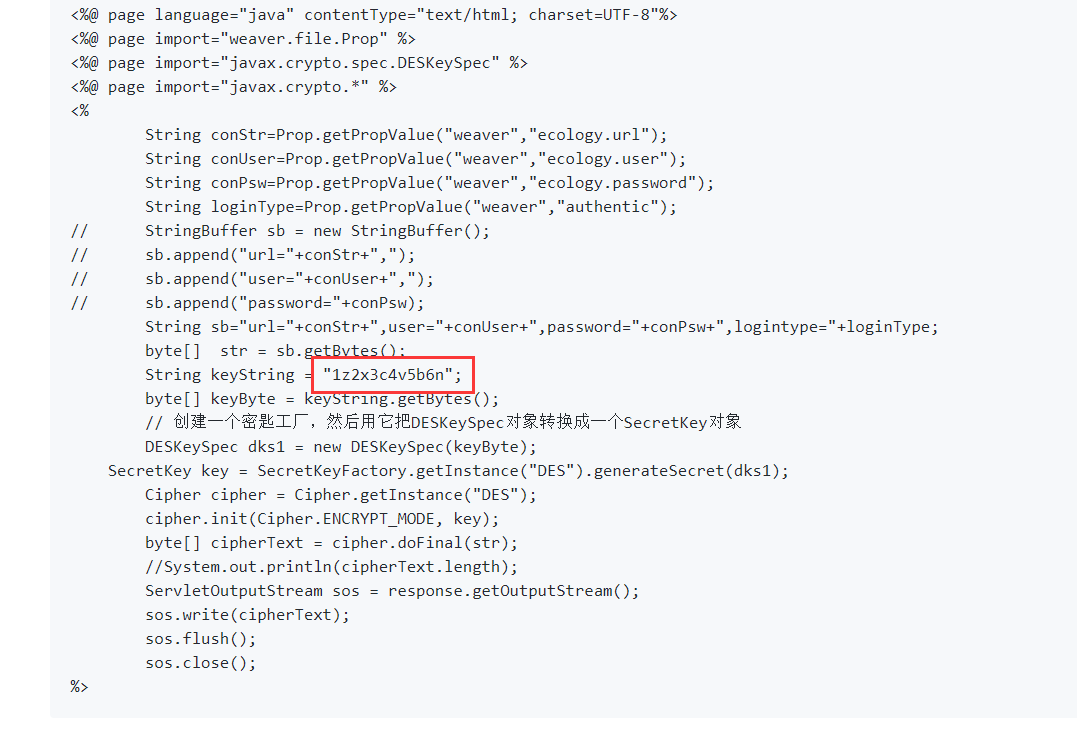
验证脚本
1 | import requests |
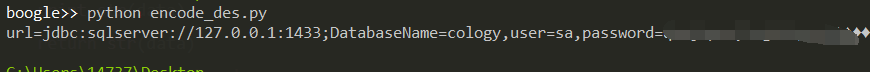
批量检测脚本
1 | import requests |
0x02 修复建议
禁止访问
mobile/DBconfigReader.jsp
0x03 参考链接
https://github.com/NS-Sp4ce/Weaver-OA-E-cology-Database-Leak/blob/master/OA.py

